Linux Administration Certification Training C ...
- 13k Enrolled Learners
- Weekend
- Live Class
Unix has started to expand its market rapidly since the past few years and is one of the Top 10 occurring IT job-requirements. So, we thought of making your job easier by making an ensemble of the most commonly asked Unix Interview Questions which will get you ready for any job interview that you wish to appear.
The following are the UNIX Interview Questions listed out for you;
Q1. Enlist common shells with their indicators.
Q2. Define a single-user system.
Q3. List a few significant features of UNIX?
Q4. What is Shell?
Q5. What are the basic responsibilities of a shell?
Q6. What is the general format of UNIX command syntax?
Q7. Describe the usage and functionality of the command rm –r * in UNIX?
Q8. Describe the term directory?
Q9. Differentiate between absolute and related path?
Q10. Which UNIX command lists files/folders in alphabetical order?
So, let’s begin.
The following table enlists the most common shells along with their indicators;
Shell | Indicators |
|---|---|
Bourne Shell | sh |
C Shell | csh |
Bourne Again shell | Bash |
Enhanced C shell | tcsh |
Z Shell | zsh |
Korn Shell | ksh |
Shell table – UNIX Interview Questions – Edureka
A personal computer which possesses an operating system designed to operate by only one user at a given time is known as a single-user system. Single user system becomes more popular since low-cost hardware and availability of a wide range of software to perform different tasks.
The following are a few features of UNIX;
Machine independent
Portability
Multi-user operations
Unix Shells
Hierarchical file system
Pipes and filters
Utilities
Development tools
The program which serves as an interface between the user and the system called a shell. It is the layer of programming that understands and executes the commands a user enters. In some systems, it’s also called a command interpreter.
Following are the responsibilities of a shell;
Program Execution
Input/ output redirection
Pipeline hookup
Environment control
Integrated programming language
Generally, UNIX shell commands follow the following pattern
Command (-argument) (-argument) (-argument) (filename)
The command rm –r * erases all files in a directory with its subdirectories.
rm is for deleting files
-r is to delete directories and subdirectories with files within
* is indicate all entries
A directory in UNIX is a specialised form of a file that maintains a list of all the files which are included in it.
Absolute path refers to the exact path as defined from the root directory whereas, related path refers to the path related to the current locations.
The ls –l command is used to list down files and folders in alphabetical order, sorted with modified time.
Another name for a file is a link. It is used to assign more than just one name for a file and is not valid to assign more than one name to a directory or to link filenames on different computers.
General command ‘– ln filename1 filename2′
A symbolic link is a file that is used to contain only the name of other files included in it. Directed to the files pointed by it is the operation of the symbolic link.
General command ‘– ln -s filename1 filename2′
FIFO or First In First Out is also known as named pipes and it is a special file for date transient. This data is read-only in the written order and is used to inter-process communications. Here data writes at one end and reads from another end of the pipe.
The command used to create a new process from an existing process is called fork(). The main process is called the parent process and new process is called child process. The parent gets the child process is returned and the child gets 0. The returned values are used to check which process which code executed.
The returned values are used to check which process is executed.
The given statement means the following;
The root account is very critical and can leads to system damage easily with abusive usage. The securities that normally apply to user accounts are not applicable to the root account. Hence, one should refrain from using root as the default login.
The Super User is a user with access to all files and commands within the system. In general, this superuser login is to root and the login is secured with the root password.
A collection of one or more processes is called a process group. There is a unique process id for each process group. The function getpgrp returns the process group ID for the calling process.
Following the different file types in UNIX;
Regular files
Directory files
Character special files
Block special files
FIFO
Symbolic links
Socket
Despite the fact that both of these commands are meant for file comparison, there still remains a fundamental difference between the two.
Cmp compares the two given files, byte by byte and displays the first mismatch.
Diff displays the changes that need to be made in order to make both the files identical.
Following are the purposes of the given UNIX commands;
The command “date” is used to retrieve the current date.
"$more README.txt“?The command displays the first part of the file names README.txt which just fit as much as on one screen.
The gzip command creates a zip file using given the filename in the same directory.
gunzip command unzip the file.
There are three parts to consider when creating/changing file access permission.
File owner’s user ID
File owner’s group ID
File access mode to define
These three parts arrange as follows.
(User permission) – (Group permission) – (Other permission)
Three types of permission can define.
r – Reading permission
w – Writing permission
x – Execution permission
The last line of a file is displayed using either “tail” or “sed” commands.
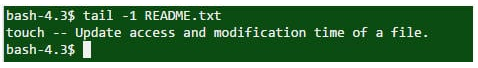
question 24 – UNIX Interview Questions – Edureka
In the example code above, the last line of the README.txt is displayed.
A process ID is a unique integer that UNIX uses to identify a certain process.
The process executes to initiate other processes is called parent process and its ID is defined as PPID (Parent Process ID).
Every process is associated with a specific user and is called the owner of the process. The owner has all the privileges over the process. The owner is also the user who executes the process.
Identification for a user is User ID. The process also associated with Effective User ID which determines the access privileges to accessing resources like files.
getpid() retrieves the Process ID
getuid() retrieves the User ID
geteuid() retrieves the Effective User ID
The Kill command accepts process ID (PID) as an in a parameter. This is applicable only for the processes owned by the command executor.
Syntax – kill PID
The main advantage is to execute processes in the background is to get the possibility to execute some other process without waiting for the previous process to get completed. The symbol “&” at the end of the process tells to the shell to execute given a command in the background.
The top command displays the CPU usage, process id, and other details.
Output
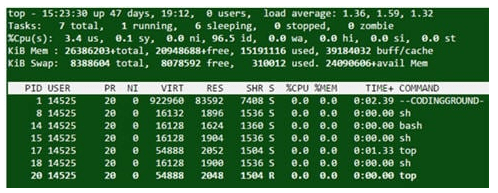
question 28 – UNIX Interview Questions – Edureka
You use ls –lrta is to display hidden files in the current directory.
Output
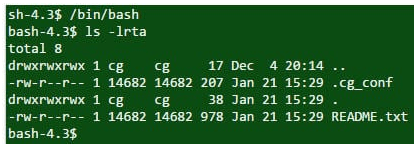
question 29 – UNIX Interview Questions – Edureka
ps –ef is a command used to find the current running process. Also, using grep with a pipe can find specific processes.
Output
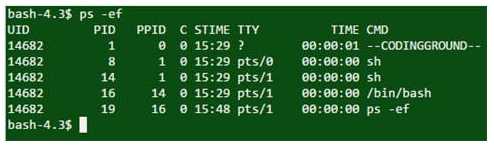
question 30 – UNIX Interview Questions – Edureka
The command df -kl is used to get a detailed description of disk space usage.
Output
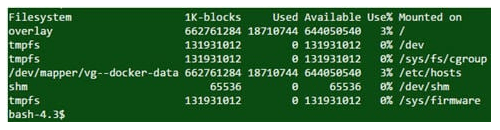
question 31 – UNIX Interview Questions – Edureka
The command mkdir directory_name is used to create a new directory.
You can use either ping or telnet to confirm a remote host is alive or not.
The history command displays all the commands used previously in the current session.
Output
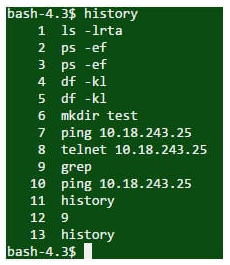
question 34 – UNIX Interview Questions – Edureka
Swapping: In this, the complete process is moved to the main memory for execution. To provide the memory requirement, process size must be less than the available main memory capacity. The implementation is easy but is an overhead to the system. Memory handling is not more flexible with swapping systems.
Paging: In this, only the required memory pages are moved to the main memory for execution. The size of the process does not a matter of execution and it no needs to be less than available memory size. Allow a number of processes to load to main memory simultaneously.
arch or uname -a can be used for the required process.
To run a process in the background, nohup is a special command. The process started with this command does not terminate even if the user logs off from the system.
The uptime command returns the number of days that the server has been up.
Output
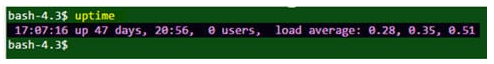
question 38 – UNIX Interview Questions – Edureka
The Kernel mode.
The echo command outputs the strings it is being passed as arguments.
When the process accesses a page which does not have access permission, it is referred to as protection fault. Also when a process attempts to write on a page whose copy on write bit was set during the fork() system call, it is incurred for protection fault.
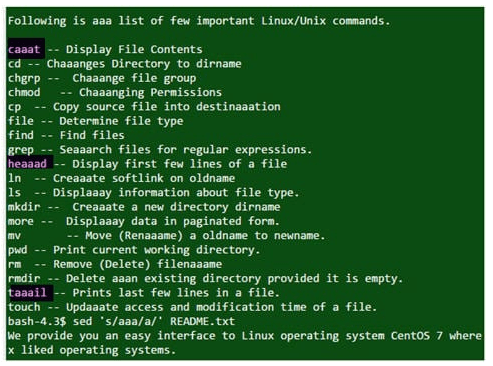
The sed command can be used for this process. In the following example, the code replaces the a‘s from the README.txt file to aaa‘s.
Example
![]()
question 42 (I)- UNIX Interview Questions – Edureka
Output
question 42 (II)- UNIX Interview Questions – Edureka
A region is a continuous area of processes address space (text, data, and stack). Regions are shareable amongst the processes.
The area contains information specific to the process and is only manipulated by the kernel. It contains the private data unique to the process allocated to u-area.
Piping(|) is used to combine two or more commands together where the output of the first command serves as the input of the second command, and so on.
The wc – c filename command can retrieve the number of characters in a file and wc –l filename command can retrieve the number of lines in a file.
The UNIX shell serves as an environment to run commands, programs, and shell scripts. In addition to that, it also acts as an interface between the user and the Unix OS. Shell issues $ as the command prompt, which reads input and determines the command to execute.
For example: $date
The command above will display the current date and time.
A Filter is described as a program, which takes input from the standard input, and displays results to the standard output by performing some actions on it.
Standard Input could be typed on the keyboard, input from other file or output of other file serving as input. Standard output is default the display screen.
The most popular example of Unix filter id grep command. This program looks for a given pattern in a file or list of files and only those lines are displayed on the output screen which contains the given pattern.
Syntax: $grep pattern file(s)
rm –r*is the command used to erase all files in the current directory including all its sub-directories.
rm: this command is used for deleting files.
-r: this option will erase all files in directories and sub-directories.
*: this represents all entries.
The Kernel is the heart of the operating system. It does not deal directly with the user but rather act as a separate interactive program for users logged in.
It is responsible for the following functions:
Interaction with the hardware
Memory management
File management
Task scheduling.
Computer resources
Allotment of resources to different tasks and users.
The key features of the Bourne shell include but aren’t limited to the following:
Input/ Output redirection.
Use of Meta-characters for file name abbreviations.
Using shell variables for the customising environment.
Creation of programs using built-in the command set.
The key features of the Korn shell include but aren’t limited to the following:
Perform command line editing.
Maintains command history so that the user can check the last command executed if required.
Additional flow control structures.
Debugging primitives who help programmers debug their code.
Support for arrays and arithmetic expressions.
Ability to use aliases which are defined as the shorthand names for command.
A variable is like a name. It is defined as a character string to which a value is assigned, where values could be the number, text, filename, etc. The shell maintains the set of internal variables as well as enables deletion, assignment, and the creation of variables.
Thus, a shell variable is a special variable that is set by the shell and is required by the shell in order to function correctly. Some of these variables are environment variables whereas others are local variables.
So, the shell variables are a combination of identifiers and assigned values that exist within the shell. These variables are local to the shell in which they are defined as well as they work in a particular way. They may have default value or values can be assigned manually by using appropriate assignment command.
To define a shell variable, the set command is used.
To delete a shell variable, the unset command is used.
Although most commonly known for analysing the input line as well as initiating the execution of the program entered by the user, the Shell has various other responsibilities. A brief description of this is given to you below;
The shell is responsible for the execution of all the programs by analysing the line and determining the steps to be performed and then initiate the execution of the selected program.
The shell allows you to assign values to the variables when specified on the command line. It also performs Filename substitution.
The shell takes care of input and output redirection.
The shell performs pipeline hook-up by connecting the standard output from the command preceding the ‘|’ to the standard input of the one following ‘|’.
The shell provides certain commands to customise and control environment.
The shell has its own built-in integrated programming language which is typically easier to debug and modify.
All data in Unix is organised into files. A file system in Unix is referred to as a functional unit or a logical collection of files, where the disk is set aside to store files and inode entries. These directories are organized into a tree-like structure called the file system. Files in Unix System are organized into multi-level hierarchy structure known as a directory tree. At the very top of the filesystem is a directory called “root” usually represented by a /.
Summarising what has been said prior to this, the file system is a collection of files and directories and has a few significant features mentioned below;
The very top of the file system is defined as the single directory called ‘root’ that contains other files and directories and is represented by an obelic sign (/).
These filesystems are self-independent and have no dependencies on other file systems.
Every file and directory is uniquely identified by the following;
The Name
The directory in which it resides
A unique identifier
All files are organised into a multi-level, hierarchical directory known as ‘Directory tree’.
When a file is created inside a directory, it accesses the two attributes, namely, file name and inode number. The file name is first mapped with Inode number and stored in the table and then this Inode number serves as a medium to access Inode. Thus, an inode can be defined as an entry created and set aside on a section of the disk for a file system. It serves as a data structure and nearly stores each information that is required to be known about a file.
This information usually includes the following details;
The File location on the disk
The Size of the file
The Device Id and Group Id
The File mode information
The File protection flags
The Access privileges for owner, group.
The Timestamps for file creation, modifications
The difference between Swapping and Paging can be seen in the table below;
| Swapping | Paging |
| It the procedure of copying the entire process from main memory onto secondary memory. | It is a memory allocation technique where the process is allocated memory wherever available. |
For execution, the whole process is moved from swap device to the main memory. | For execution, only the required memory pages are moved from swap device to the main memory. |
The than main memory. process size must be equal to or less | The process size does not matter in this case. |
It cannot handle the memory flexibly. | It can handle the memory more flexibly. |
table 2 – UNIX Interview Questions – Edureka
The kernel is the heart of the operating system. It is the lowest level of the operating system and is responsible for translating the command into something that can be understood by the computer. The resources allocation to different users and tasks handled by this section. The kernel doesn’t have any direct communication with the user and so, it starts a separate interactive program called the shell to each user when login to the system.
Some commonly used networking commands in Unix are enlisted below:
telnet: This command is used for remote login as well as for communication with another hostname.
ping: This command is defined as an echo request for checking network connectivity.
su: This command is derived as a user switching command.
hostname: This command determines the Ip address and domain name.
nslookup: This command performs a DNS query.
xtraceroute: This command is used to determine the number of hoops and response time required to reach the network host.
netstat: This command provides a lot of information like ongoing network connection on the local system and ports, routing tables, interfaces statistics, etc.
There are essentially three types of accounts in the Unix operating system;
The Root account
The System accounts
The User accounts
Amongst the aforementioned, the Root account is commonly referred to as the Superuser. This user has a completely open access on all files and commands on the system. This superuser account can also be assumed as a system administrator and hence, has the ability to run any command without any restriction. It is protected by the root password.
When two or more commands are required to be used at the same time as well as run consecutively, you use an operator known as the pipe(|). What it does is it connects two commands in such a fashion that, the output of one program serves as the input for another program.
Enlisted below are a few commands where the pipe operator is used;
grep command: searches files for certain matching pattern.
sort command: arranges lines of text alphabetically or numerically.
In a file system for any operating system, there exists the hierarchy of directories, there ‘Path’ is defined as the unique location to a file/ directory to access it.
There are basically two types of pathnames that are used in Unix. These can be defined as follows:
A SuperBlock is essentially a program that contains a record of specific file systems.
Characteristics such as the block size, the empty and the filled blocks and their respective counts, the size and location of the inode tables, the disk block map, and usage information, and the size of the block groups are available in a superblock.
There are basically two types of superblocks which are the following;
Default superblock: It has its existence always as a fix offset from the beginning of the system’s disk partition.
Redundant superblock: It is referenced when the default superblock is affected by a system crash or some errors.
Here are some filename manipulation commands along with their description, enlisted in the table below;
Command | Description |
|---|---|
cat filename | Displays contents of the file |
cp source destination | Used to copy the source file into the destination |
mv old name new name | Move/rename and old name to the new name |
rm filename | Remove/delete filename |
Touch filename | Changing modification time |
In [-s] old name new name | Creates soft link on old name |
Is –F | Displays information about file type |
table 3 – UNIX Interview Questions – Edureka
Links are called as a second name which is used to assign more than one name to a file. Although links are referred to as a pointer to another file it cannot be used to link filenames on different computers.
A Symbolic link is also known as the soft link is defined as a special type of file that contains links or references to another file or directory in the form of an absolute or a relative path. It does not contain the data actually in the target file but the pointer to another entry in the file system. Symbolic links can be used to create a file system, too.
The following command is used to create a symbolic link;
Ln –s target link_name
Here, path is ‘target’
Name of the link is represented by link_name.
To avoid typing long commands or to improve efficiency, the alias command is used to assign another name to a command. Basically, it acts as a shortcut to the larger commands which can be typed and run instead.
For creating an alias in Unix, following command format is used:
alias name=’command you want to run’
Here, replace the ‘name’ with your shortcut command and replace ‘command you want to run’ with the larger command of which you want to create an alias of.
For example:
alias dir ‘Is –sFC’
here, in the example above, dir is another name for the command Is-sFC. Thus, the user now simply is required to remember and use the specified alias name and the command will perform the same task as to be performed by the long command.
Wildcard characters are some special kind of characters that represent one or more other characters. Wildcard interpretation comes into the picture when a command-line contains these characters. In this case, when the pattern matches the input command, these characters are replaced by a sorted list of files.
The Asterisk(*) and Question mark(?) are usually used as wildcard characters to set up a list of files while processing.
System calls: As the name implies, system calls are defined as an interface which basically is used in the kernel itself. Although, they may not be fully portable but these calls request the operating system to perform tasks on behalf of user programs.
The system calls appear as a normal C function. Whenever a system call is invoked within the operating system, the application program performs context switch from user space to kernel space.
Library functions: The set of common functions that are not part of the kernel but is used by the application programs are known as ‘Library functions’. As compared to system calls, library functions are portable and can perform certain tasks only in ‘kernel mode’. Also, it takes lesser time for execution as compared to the execution of system calls.
A PID is used to denote a unique process id. It basically identifies all the processes that run on the Unix system. It does not matter whether the processes are running in the foreground or in the background.
Kill() system call is used to send signals to any processes.
This method returns the following return values;
Returns 0: It implies that the process exists with the given PID and the system allows sending signals to it.
Return -1 and errno==ESRCH: It implies that there is no existence of the process with specified PID. There may also exist some security reasons which is denying the existence of the PID.
Return -1 and errno==EPERM: It implies that there is no permit available for the process to be killed. The error also detects whether the process is present or not.
EINVAl : it implies an invalid signal.
The various commands that are used for displaying the user information in Unix are enlisted as follows;
id: This command displays the active user id with login and group.
last: This command displays the last login of the user in the system.
who: This command determines who is logged onto the system.
groupadd admin: This command is used to add group ‘admin’.
usermod –a: This command is used to add an existing user to the group.
‘tee’ command is basically used in connection with pipes and filters.
This command basically performs two tasks:
a) Get data from standard input and send it to the standard output.
b) Redirects a copy of the input data to the specified file.
Mount command: As the name suggests, the mount command mounts a storage device or file system onto an existing directory and thus making it accessible to users.
Unmount command: This command unmounts the mounted file system by safely detaching it. It also the task of this command to inform the system to complete any pending read and write operations.
Chmod command is used to change file or directory access permission and is the most frequently used command in Unix. According to mode, chmod command changes the permission of each given file.
The syntax of chmod command is:
Chmod [options] mode filename.
Here in the above format, options could be:
-R: recursively change the permission of file or directory.
-v: verbose, i.e. output a diagnostic for every file processed.
-c: report only when the change is made.
Command substitution is a method which is performed every time the commands that are enclosed in back-quotes are processed by the shell. This procedure replaces the standard output and displays on the command line.
Command substitution can perform the following tasks;
Invoke sub-shells
Result in word splitting
Remove trailing new lines
Allow setting a variable to the content of the file by using ‘redirection’ and ‘cat’ command
Allow setting a variable to the output of the loop
These were all the UNIX interview questions we could think of. These UNIX interview questions would cover you for any interview you’d appear for, in the shortest possible time frame. If you have any interesting questions that have been asked to you in an interview you’ve appeared before, feel free to drop them at the comments bar and we shall answer them for you. You could also refer to this video which explains the solutions to these problems in depth.
| Course Name | Date | |
|---|---|---|
| Linux Administration Certification Training Course | Class Starts on 18th February,2023 18th February SAT&SUN (Weekend Batch) | View Details |
| Linux Administration Certification Training Course | Class Starts on 29th April,2023 29th April SAT&SUN (Weekend Batch) | View Details |
 REGISTER FOR FREE WEBINAR
REGISTER FOR FREE WEBINAR  Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUP
Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUP
edureka.co
