DevOps Certification Training Course
- 139k Enrolled Learners
- Weekend/Weekday
- Live Class
Higher the use of technology, greater the possible threat to security. A typical Ansible set up requires you to feed-in “Secrets”. These secrets could be literally anything, passwords, API tokens, SSH public or private keys, SSL certificates, etc. How do we keep these secrets safe? Ansible provides with a feature called Ansible Vault.
In this blog, I’ll demonstrate how to use Ansible Vault and explore some of the best practices for keeping the data safe.
Topics covered in this blog:
If you wish to master DevOps, this course would be your go-to option.
Having infrastructure as code can pose the threat of exposing your sensitive data to the world, leading to unwanted security issues. Ansible Vault is a feature that allows you to keep all your secrets safe. It can encrypt entire files, entire YAML playbooks or even a few variables. It provides a facility where you can not only encrypt sensitive data but also integrate them into your playbooks.
Vault is implemented with file-level granularity where the files are either entirely encrypted or entirely unencrypted. It uses the same password for encrypting as well as for decrypting files which makes using Ansible Vault very user-friendly.
As Ansible is being used for automation, there is a high possibility that playbooks contain certain credentials, SSL certificates or other sensitive data. Saving such sensitive data as plain text is a bad idea. One wrong commit to GitHub or laptop theft can cause an organization a huge loss. This is where Ansible vault comes into the picture. It is a great way of having infrastructure as code, without compromising on the security.
Suppose, we have a playbook that provisions your EC2 instance on AWS. You need to provide your AWS access key id and AWS secret key in the playbook. You do not share these keys with others for obvious reasons. How do you keep them unexposed? There are two ways – Either encrypt these two variables and embed them into the playbook or encrypt the entire playbook.
This was just one of the scenario where ansible vault can be used. We can either encrypt entire files or just encrypt few variables which might hold sensitive data and then Ansible automatically decrypts them during runtime. Now we can safely commit these values to GitHub.
To create an encrypted file, use the ansible-vault create command and pass the filename.
$ ansible-vault create filename.yamlYou’ll be prompted to create a password and then confirm it by re-typing it.
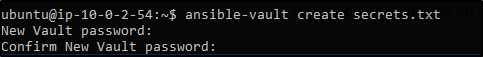
Once your password is confirmed, a new file will be created and will open an editing window. By default, the editor for Ansible Vault is vi. You can add data, save and exit.

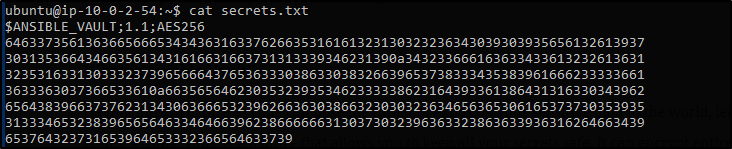
If you want to edit an encrypted file, you can edit it using ansible-vault edit command.
$ ansible-vault edit secrets.txtWhere secrets.txt is an already created, encrypted file.
You’ll be prompted to insert the vault password. The file(decrypted version) will open in a vi editor and then you can make the required changes.
![]()
If you check the output, you’ll see your text will be encrypted automatically when you save and close.

If you wish to just view an encrypted file, you can use the ansible-vault view command.
$ ansible-vault view filename.yml
Again you’ll be prompted for a password.
![]()
and you’ll see similar output.

Of course, there are times where you’ll want to change the vault password. You can use the ansible-vault rekey command.
$ ansible-vault rekey secrets.txtYou’ll be prompted with the vault’s current password and then the new password and finally done by confirming the new password.

Suppose you have a file which you wish to encrypt, you can use the ansible-vault encrypt command.
$ ansible-vault encrypt filename.txtYou’ll be prompted to insert and confirm password and your file is encrypted.

Now that you look at file contents, its all encrypted.

If you want to decrypt an encrypted file, you can use ansible-vault decrypt command.
$ ansible-vault decrypt filename.txtAs usual, it’ll prompt you to insert and confirm the vault password.

Best practice while using Ansible Vault is to encrypt only the sensitive data. In the example explained above, the development team does not want to share their password with the production and the staging team but they might need access to certain data to carry out their own task. In such cases you should only be encrypting the data you do not want to share with others, leaving the rest as it is.
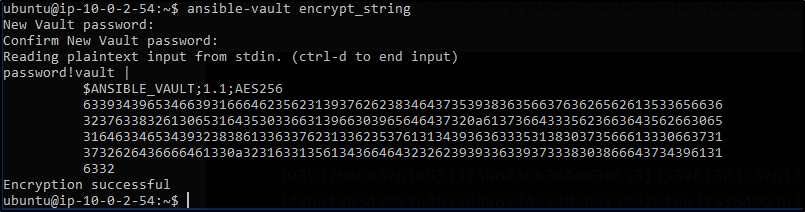
Ansible Vault allows you to encrypt only specific variables. You can use the ansible-vault encrypt_string command for this.
$ ansible-vault encrypt_stringYou’ll be prompted to insert and then confirm the vault password. You can then start inserting the string value that you wish to encrypt. Press ctrl-d to end input. Now you can assign this encrypted value to a string in the playbook.
You can also achieve the same thing in a single line.
$ ansible-vault encrypt_string 'string' --name 'variable_name'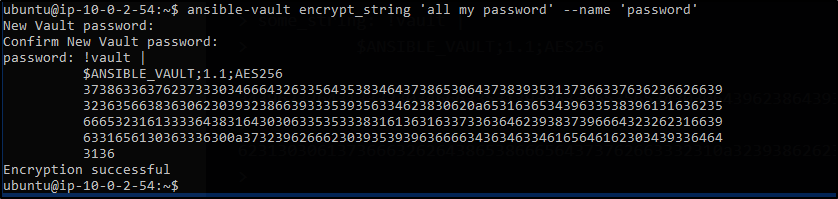
If you wish to decrypt a file during runtime, you could use –ask-vault-pass flag.
$ ansible-playbook launch.yml --ask-vault-passThis will decrypt all the encrypted files that are used for this launch.yml playbook to execute. Also, this is only possible if all the files are encrypted with the same password.
![]()
Password prompts can get annoying. The purpose of automation becomes pointless. How do we make this better? Ansible has a feature called “password file” which references to a file containing the password. You can then just pass this password file during runtime to automate it.
$ ansible-playbook launch.yml --vault-password-file ~/ .vault_pass.txt![]()
Having a separate script that specifies the passwords is also possible. You need to make sure the script file is executable and the password is printed to standard output for it to work without annoying errors.
$ ansible-playbook launch.yml --vault-password-file ~/ .vault_pass.pyVault Id is a way of providing an identifier to a particular vault password. Vault ID helps in encrypting different files with different passwords to be referenced inside a playbook. This feature of Ansible came out with the release of Ansible 2.4. Prior to this release, only one vault password could be used in each ansible playbook execution.
So now if you wish to execute an Ansible playbook which uses multiple files encrypted with different passwords, you can use Vault Id.
$ ansible-playbook --vault-id vault-pass1 --vault-id vault-pass2 filename.ymlWith this, we come to the end of this Ansible Vault blog. It is amazing to catch up with technology and make the fullest of them but not by compromising on security. This is one of the best ways to have Infrastructure as code(IaC).
If you find this article helpful, check out the DevOps course offered by Edureka. It covers all the tools that have made the IT industry smarter.
Got a question for us? Please post it on Edureka Community and we will get back to you.
| Course Name | Date | |
|---|---|---|
| DevOps Certification Training Course | Class Starts on 21st January,2023 21st January SAT&SUN (Weekend Batch) | View Details |
| DevOps Certification Training Course | Class Starts on 30th January,2023 30th January MON-FRI (Weekday Batch) | View Details |
| DevOps Certification Training Course | Class Starts on 20th February,2023 20th February MON-FRI (Weekday Batch) | View Details |
 REGISTER FOR FREE WEBINAR
REGISTER FOR FREE WEBINAR  Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUP
Thank you for registering Join Edureka Meetup community for 100+ Free Webinars each month JOIN MEETUP GROUP
edureka.co
